Business Email Compromise (BEC) is one of the most costly and pervasive scams out there. It wears many faces – sometimes it’s a fake invoice from a company supplier, other times scammers impersonate bosses and executives to scam a business. But scammers can also exploit the very tools we rely on to run our businesses.
Recently, a member of the community shared a case that perfectly captures how subtle, targeted, and dangerous BEC can be: a phishing email disguised as a Zoom meeting invite. On the surface, it looked like a routine client meeting request. In reality, it was a scam in disguise where one click installed a remote access tool that gave scammers control of the computer before anyone realized what had happened.
What Exactly is BEC?
Business Email Compromise, or BEC, is a form of cybercrime where attackers use email to trick businesses into transferring money, revealing sensitive information, or granting system access. Unlike broad-scale phishing campaigns, BEC attacks are scams with a business plan. They’re highly researched, targeted, and have a specific end goal in mind.
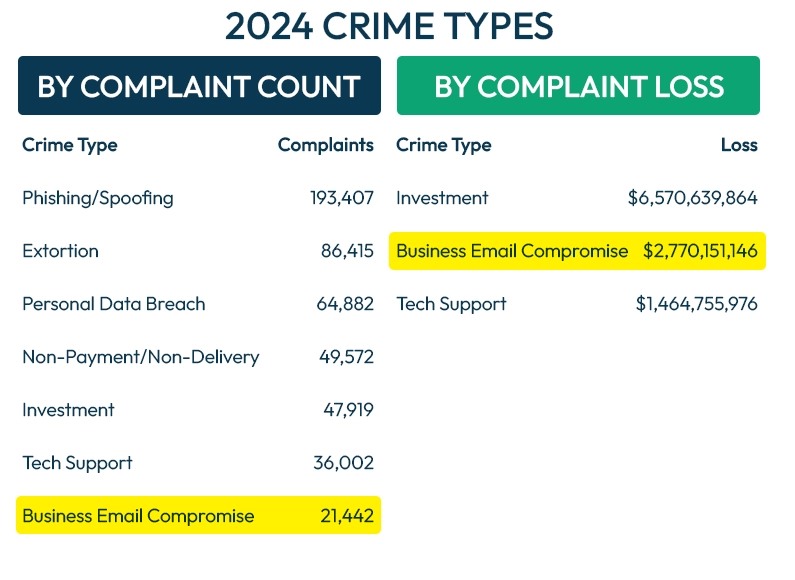
These attacks are also very costly. According to the FBI’s IC3 2024 Annual Report, BEC was the 7th most reported complaint last year. While it didn’t top the charts in volume of complaints, it did have a massive financial impact. Coming in second behind investment scams for total losses, BEC accounted for $2.8 billion lost in 2024 alone, and a staggering $8.5 billion in reported losses over just three years.
Those billions in losses reflect a bigger truth – BEC scams are happening every day to businesses of all sizes across every industry. The attacks don’t always scream “fraud” or “scam”, but that’s because they are often designed to blend into ordinary workflows and business processes. One such attack, shared with us by a member of the Kitboga community, illustrates just how seamless and damaging these scams can be.
A Scam Disguised as a Zoom Meeting
The targeted business regularly meets with clients online through Zoom, so when a “customer” sent a meeting link by email to an employee’s personal computer, it didn’t raise any eyebrows.
But this wasn’t Zoom at all. The link led to an installer for a remote access tool – legitimate software used by scammers for malicious purposes. Clicking it installed a program that gave the scammer access to the laptop, letting them control it as if they were sitting right in front of it themselves from wherever they were in the world.
This wasn’t malware or some sophisticated hack, it was social engineering with a software assist, resulting in a smooth hand-off of control of the device to someone with bad intentions.
Read more about remote access software and how scammers use it: Behind the Screen: The Dangers of Remote Connection
Once connected, the scammers took over the screen, displaying a fake “Windows Updates Downloading” message to hide their activity while they worked. Fortunately, the victim knew something was wrong and contacted IT before things escalated.
Breaking Down the Fake Zoom Invite Email
Here’s the actual phishing email that was sent (sensitive details blurred):
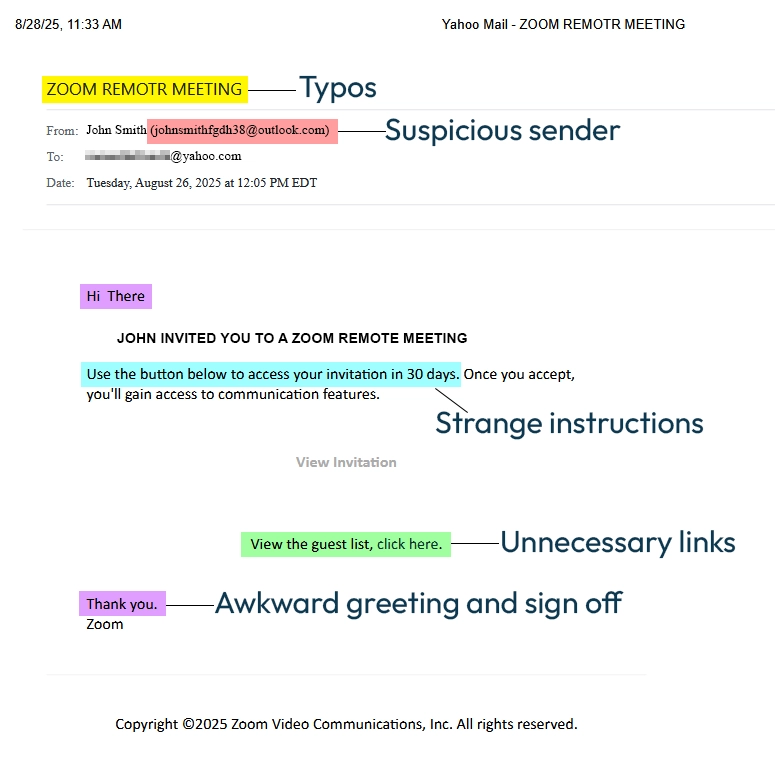
At first glance, it looks like a Zoom meeting request. But on closer inspection, several details give away the scam.
Typos. The subject line reads “ZOOM REMOTR MEETING” – One letter off. So close!
Suspicious sender. The email came from a personal outlook address even though they were posing as Zoom, not from Zoom’s official @zoom.us domain.
Strange instructions. “Use the button to access your invitation in 30 days.” Real Zoom emails don’t use phrases like this.
Unnecessary links. Asking you to “view the guest list” or “view the invitation” is not part of standard Zoom invites.
Awkward greeting and sign off. Zoom doesn’t start emails with “Hi There” (why the weird spacing?) or end with “Thank you.”
The Devil is in the Domain
Perhaps the biggest (but not the most obvious) sign was the link destination. Hovering over the “View Invitation” link revealed the destination wasn’t Zoom at all, but a lookalike domain – zoomnivite.com (with yet another spelling mistake). Real Zoom links always use zoom.us.
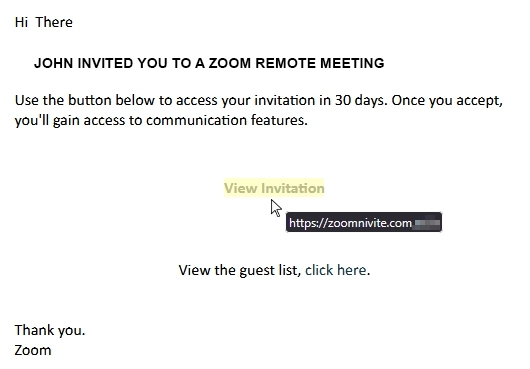
One of the most convincing tactics in scams like this is the use of lookalike domains – emails and website links that appear legitimate at first glance but are slightly off. It might be a single swapped letter, an extra or missing character, or a different domain (.co instead of .com), just subtle enough to not draw attention – and human eyes are surprisingly easy to trick.
For comparison, a real Zoom link and email would look more like this:
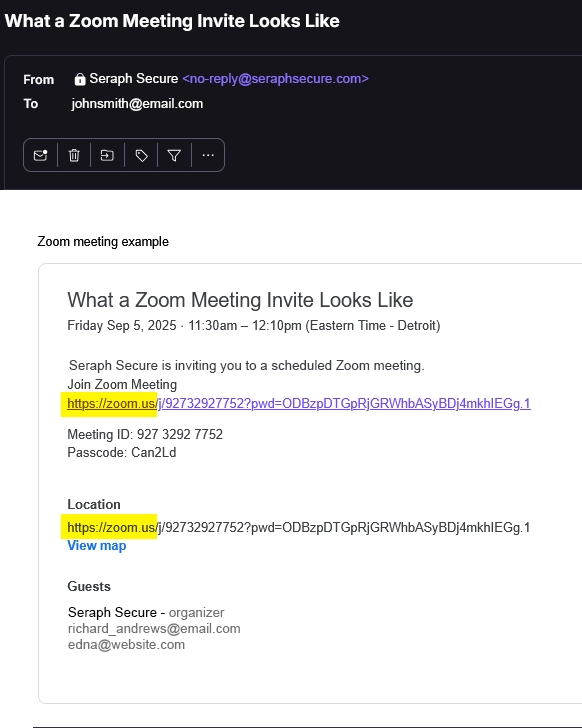
How Spear Phishing Makes BEC Work
Many phishing emails work like spam – scammers cast a wide net, blasting out generic messages to thousands of people and hoping someone, somewhere, will click or respond. Spear-phishing is different. It’s research-driven and doesn’t rely on luck alone. Instead, attackers gather details about a company’s operations, tools, and staff. Then, they use what they learn to impersonate trusted names, roles and everyday workflows to target employees with very specific, tailored messages.
This type of scam is common in the business world where a little research can have big payoffs for scammers. By mimicking normal business requests, they exploit human trust and can dupe even the most experienced employees.
That’s exactly what happened here. The scammers used spear-phishing tactics, gathered background details about how the company operated, and then targeted one employee, relying on their trust in familiar tools, customers, and routines. They knew this business used Zoom for meetings which was just enough insight to make this fake invite believable enough for someone to click.

Staying One Step Ahead of BEC
BEC isn’t slowing down anytime soon. These attacks hit businesses of all sizes, as well as government agencies, nonprofits, and even school districts and universities. If your organization manages money or sensitive operations, you’re a target. Defense requires a blend of awareness, verification, and layered security measures.
Scammers count on you being busy or distracted and not taking time to verify information and requests. Before you click or act, hover over links and double-check the full email address. Is it really from the person or company it claims to be? If it’s any sort of monetary or payment request, verify with the person directly before acting.
When it comes to fake emails, small details are often the only warning signs you’ll get, but a few extra seconds of checking could save you from becoming the next BEC success story.
– The Seraph Secure Team