Scammers don’t need to hack your computer – they just ask for access. And more often than not, people say yes. With the right script and a false sense of urgency, a scammer can talk their way into your device with just a few clicks, gaining total control before you even realize what’s happening. Remote access scams are on the rise, and the consequences go far beyond a single bad day.
Remote connection software – also known as remote access, remote desktop, or remote control tools – allows someone to control a computer from virtually anywhere in the world.
These tools have revolutionized how we troubleshoot tech problems and collaborate across distances. Whether you’re helping a relative fix their computer, logging into your work computer from home, or accessing your personal files while vacationing on a faraway island, remote access software can make life easier.
But with that convenience comes risk.
Unfortunately, scammers have also embraced remote connection tools – not to help, but to harm. With a bit of persuasion and social engineering, they convince unsuspecting victims to hand over total control of their computers, often resulting in serious financial loss, identity theft, and long-lasting consequences.
The Basics of Remote Connection
At its core, remote connection software lets one device control another over the internet. Letting someone access your computer remotely is a bit like handing a stranger your house keys and saying “let yourself in whenever you like” or giving someone your unlocked phone and telling them to freely browse through your messages, photos, apps, and private notes. You’re essentially doing that with your computer, but without realizing how much power you’re giving away.
How Remote Connection Software Works
You can download and install remote connection software from any number of companies like AnyDesk, TeamViewer, Supremo, and HopToDesk. Many offer these tools free for personal use.
The software generates a unique code or PIN that you share with the person you want to connect with. The code allows them to connect to your device. In a legitimate situation, you might share this with an IT technician or a family member helping you with tech support.
The other party enters the code to bridge the two devices. Once connected, the remote user gains access to your computer and takes control – they can move your mouse, open files, install programs, and more, all in real-time, as if they were sitting in front of your own screen.
These tools can be incredibly useful when used by people you trust. But in the wrong hands? They become a nightmare.
Where Scammers Come In
Scammers use the convenience of remote access software and weaponize it against their victims. Through fear, confusion, faked urgency, and false reassurance, they manipulate people into letting them on their devices.

Here are some of the more common scenarios where scammers use remote access tools as part of their scams. This is not an exhaustive list – many different types of scammers will look for the opportunity to connect to a victim’s device if they can.
Tech Support Scams:
Scammers pose as tech support agents claiming your computer is infected with a virus or has been hacked. They convince you to let them connect to “fix” the problem.Refund Scams:
Pretending to be from a company or your bank, scammers offer to issue a refund. They claim they need access to verify details or process the transaction.Investment Scams:
Scammers impersonate financial advisors and connect to your computer to guide you through fake investment platforms.Prize Scams:
Scammers say you’ve won a prize, but request remote access so they can help you claim it.

While their excuses and scripts may vary, the goal is the same: gaining full, unrestricted access to your computer. Once you’re convinced – or scared enough into complying – they’ll guide you through downloading software onto your device.
The True Danger of Remote Connection Software Abuse
Here’s the problem – letting a scammer connect to your computer has more consequences than the surface-level threat of losing money in the moment. It opens the door you’ve unknowingly created and gives them unrestricted access to your entire life, putting you at risk to be further scammed or having your identity stolen.
Scammers know the value of having this connection to their victims because it gives them direct access to your most sensitive data.
Once a scammer is on your device, they can:
Steal personal information and saved passwords
Access bank accounts and private files
Get into your email and social media
Install malware, spyware, or keyloggers
Monitor your activity and spy through your webcam
Lock you out of your own device
Scammers will reassure victims to keep them calm, even while they’re silently digging into the most sensitive places on your computer. They may assure victims that they can’t see the screen, that everything is secure, or that they’re working on your computer so they can get rid of the hackers, processing your refund, or helping you check your bank account for unauthorized charges.
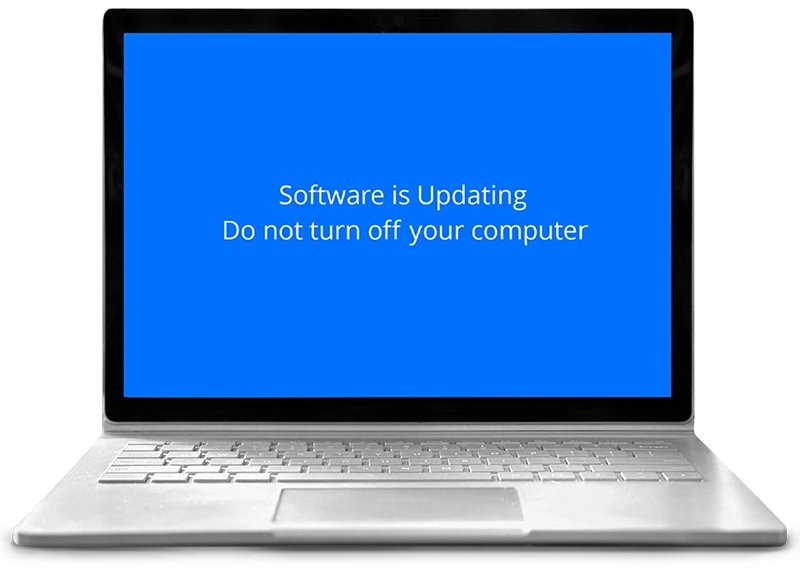
Many remote connection software comes with a feature that scammers use to black out your screen or hide it behind a fake “Windows Update” so you can’t see what they’re doing which makes the deception seamless.
Unattended Access: When Things Go from Bad to Worse
Some scammers go a step further. If they get into the device once, they make sure they can come back whenever they want.
They can do this because many remote connection tools offer a feature called “unattended access”. This allows someone to reconnect to your computer whenever they want, even without your knowledge or permission. These scammers can sit in the background of your computer watching your every move for days, months, or even years, all without being obvious to the average user.
Watch the video below to see what can happen if scammers have unrestricted access to your computer:
Antivirus Software will NOT Help
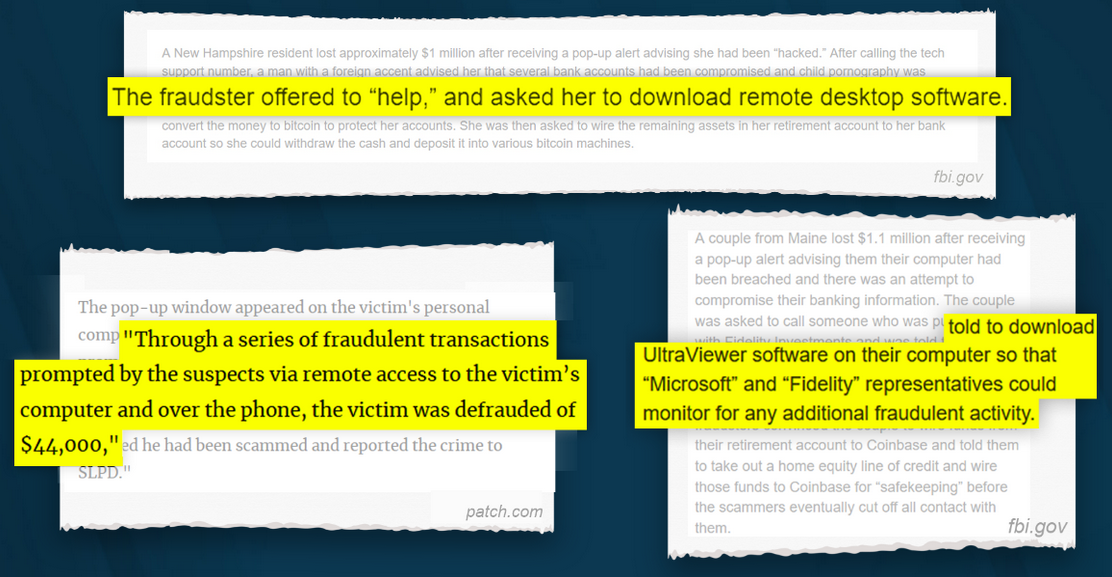
Many consumer protection agencies and financial institutions tell scam victims to “run an antivirus scan” or “update securities” on their computer as a standard step to take post-scam. While this advice comes from a good place, it falls short.
Remote connection software is not a virus. It’s a legitimate program that security software won’t see as a threat. Even an up-to-date, premium antivirus program may not catch it. That’s one of the many reasons scammers love it – it flies under the radar, even on a “protected” computer.
This creates a dangerous gap in current guidance: victims are left thinking they’re secure, while the scammer still has a backdoor into their lives.
How to Protect Yourself
Never give remote access to your device unless you initiate contact and fully trust the person or organization. Think of it like giving someone access to your finances or home – you are giving someone access to everything on your computer – it’s not something to do lightly.
Be skeptical of any unsolicited calls, emails, or text messages offering help for some sort of problem. If someone claims to represent a trusted organization, independently verify their identity by contacting the company through their official channels.
Tip from the scam experts: Companies like Microsoft, Apple, Norton, Geek Squad, etc. don’t know when your computer has a virus.Use software built to defend against remote access scams. Seraph Secure offers a free tool that scans your device for any existing remote access software a scammer may have installed and gives you the option to remove it. It also blocks any new remote connection attempts. You don’t need to be tech-savvy to use it – just install and let it run in the background where it will quietly shield your device from remote access threats.
Educate yourself and others. Scammers often target individuals, especially senior citizens, who are unfamiliar or uncomfortable with technology. Sharing information about the dangers of letting a stranger connect to your devices may save someone from becoming a victim.
Don’t Wait Until It’s Too Late
Remote access can be a powerful tool when it is used correctly. But in the wrong hands, it becomes a gateway to more scams, identity theft, and long-term damage.
If you’ve already been targeted or just want to protect yourself from the growing threat of remote access scams, Seraph Secure can help. Get it for free and keep scammers off your devices.
Don’t wait until you or someone you love becomes the next target. The convenience of remote connection software should never come at the cost of your online safety or peace of mind. Whether you’re protecting yourself, a parent, or a friend, Seraph Secure can help.
Seraph Secure is designed specifically to close the gap that traditional antivirus software misses. It’s free, easy to use, and built to protect you from the threat of remote access.
You wouldn’t hand your house keys to a stranger. Don’t do it with your computer.
Download Seraph Secure today and take back control – before someone else takes it from you.